Argentum IT LLC Blog
Using 2017's Examples to Maintain Network Security in the New Year
Network security is a crucial consideration for every single business, especially ones that utilize the Internet. There were a lot of negatives and some positives that came out of 2017 in regards to cybersecurity. Below we have listed some of the most troubling cybersecurity statistics collected in 2017, and we’ve followed it up with suggestions on how to keep your business safe in 2018.
Statistic for 2017: In the United States, 61% of small businesses experienced a cyberattack and 54% experienced a data breach that had severe financial consequences in 2017. This year saw phishing/social engineering scams out number web-based attacks for the first time. Phishing (or the attempt to use fraudulent emails that look legitimate to obtain sensitive information to exploit for financial gain), and social engineering (or the psychological manipulation that persuades others into offering personal information), make up about 48% of all cyberattacks.
SMB Action for 2018: One way to reduce the risk that your company will fall victim to phishing and social engineering to make sure that your employees are aware of up-to-date cybersecurity best practices and follow them at all times. Even something as simple as opening an email attachment can have a catastrophic impact on your business. Creating a Acceptable Use of Technology policy is a great way to make sure that your employees know what is expected of them when it comes to technology and your business.
Statistic for 2017: Despite that fact that many business owners feel like their employees and/or contractors would never do anything to cause data loss or put their network at risk, more than half (54%) of the data breaches for small business in 2017 came from employee/contractor negligence, up from just 48% the previous year. While negligence was at the top of the list of was followed closely by third party mistakes (43%) and errors in system or operating processes (34%). Surprisingly, however, nearly ⅓ of those companies who experienced a breach stated that their company could not determine what caused the incident.
SMB Action for 2018: Short of having a computer forensics unit on standby, businesses will need to improve their resilience by properly training their staff in, at the very least, the industry standard of protecting an organization’s network. Enforcing strict guidelines on how people access and interact with data will go a long way toward mitigating organizational risk. Employing the use of virtual private networks (VPNs) to encrypt remote access data flow provides a strong defense against the interception of data.
Organizations will also need to follow strict procedure to close any vulnerabilities they may have with software systems, or former employee, contractor, or vendor access to their network infrastructure. The more diligent organizations are in training staff, and enacting a fast-acting strategy against closing vulnerabilities, the better chance they have of coming through 2018 unscathed.
Statistic for 2017: One question that is frequently overlooked during most run-of-the-mill security surveys is what it is that small businesses believe to be the most likely target of cybercrime attacks on their business - and are therefore most likely to be protected by SMBs. According to the results of this survey, about 63% of small business owners felt that the theft of their customer records was of primary concern. Followed by the theft of their intellectual property at 48%.
SMB Action for 2018: Since the protection of all data depends on diligence, protecting customer records, intellectual property, as well as employee’s personal information and the organizational financials is really a large effort that has to be understood and performed by every single person in your organization. Companies today are constantly under threat and have to organize their security strategy to be both proactive and reactive. Hackers know what they’re looking for and designing a strategy and following through is the only way the modern organization is going to be able to protect itself 100% of the time.
Statistic for 2017: When it comes to detection and prevention, small business technology scored rather dismally. In fact, 61% of small businesses responded that the technologies currently in use by their organization could NOT detect and block most cyberattacks. For 2017, 66% of responding businesses said that they had already experienced exploits and malware attacks that had evaded the current intrusion detection systems, if they had any to speak of and 81% had attacks evade their anti-virus solutions.
SMB Action for 2018: Today’s RMM tools, firewalls, and antivirus programs are thorough, but are often not always updated in real time. Today it is important to depend on solutions that don’t keep you at risk long than you need to be. Companies will have to invest time and capital into defending themselves in 2018, just as they have had do to over the past several years. There is some real risk that relying on software alone will catch most of the threats, but only an actively monitored network is truly safe.
Statistic for 2017: When it comes to ransomware, the majority of small businesses that have not yet been victims of ransomware still believe that they are too insignificant in size to be targeted by cybercriminals. Less than 50% of small business respondents said that ransomware was a serious financial threat, were concerned that negligent employees put their company at risk, and felt that the prevention of these types of attacks were a priority.
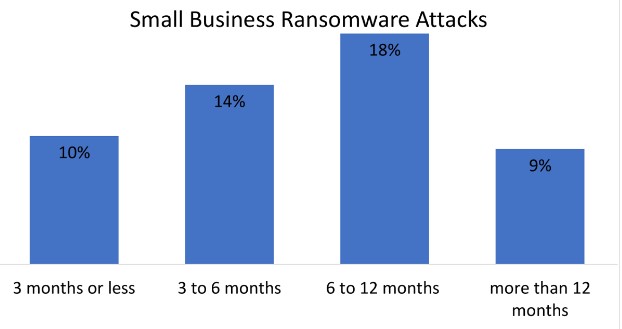
Of those SMBs that have been victims of one or more ransomware attacks, 51% that it was within the past twelve months or less. With 10% experiencing attacks in the past three months or less, 14% within 3 to 6 months, 18% within 6 to 12 months and 9% within 12 months or more. There were three predominant types of ransomware reported by those who were attacked. 39% were faced with encryption ransomware, 30% were faced with locker ransomware and 31% were faced with both.
SMB Action for 2018: Ransomware can be a business ruiner, period. In 2018, companies will have to come to grips with the new normal in which many different strands of ransomware will be available to hacker all over the world. Furthermore, companies will have to consider themselves the prime target for this type of threat. If over a third of businesses are exposed to some fashion of ransomware, expect that number to rise exponentially. It is a problem that has to be at the forefront of any organization's cybersecurity considerations in 2018.
Statistic for 2017: In one of the most concerning aspects of this extremely informative study, of those small businesses who were attacked more than 60% paid the ransom. The average ransom paid out was $2,157. Of the 40% who did not pay, they cited the following reasons for not paying: 67% said it was because they had a full backup and would not lose the data and 52% said they did not trust the criminals provide the decryption cypher upon payment.
SMB Action for 2018: First, it must be made clear that UNDER NO CIRCUMSTANCES SHOULD A SMALL BUSINESS PAY A RANSOM. Ransomware attacks are becoming less and less likely to return data after payment. In fact, many businesses are faced with multiple payments that culminate in data loss AND significant monetary damages. Small businesses can no longer afford not to have both a security solution that helps them keep ahead of the latest ransomware threats, as well as data backup solutions that will be there to fall back on in the event that ransomware does get the best of them. For those businesses who felt that they couldn’t afford to have a data recovery and network security solutions in the past are now finding that they can’t afford not to.
Statistic for 2017: It seems like each year, there are more government compliance and regulatory standards that small business technology is required to meet. For example, the Health Insurance Portability and Accountability Act (HIPAA) has made a lot of headlines over the past several years, demanding that healthcare facilities take certain precautions when it comes to the management of electronic health records. However, a surprising amount of small businesses have yet to experience government enforced standards for their industry. 41% of all small businesses say they do not have to comply with any type of standard or guideline.
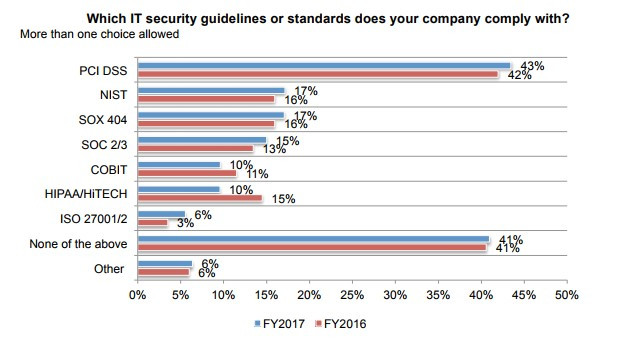
SMB Action for 2018: Network security cannot be thought of as optional. Just because your industry or business doesn’t fall under the umbrella of federal or state data security mandates, doesn’t mean that you should look at network security as unimportant. We’ve outlined through this article just how difficult sustaining a business is when you lose any data, let alone customer or vendor data. With 41% of surveyed companies not complying with even payment card index regulation, there is likely an opportunity for your organization to enhance its network security efforts. Hackers and social engineers aren’t becoming less prevalent, so the modern business should absolutely act accordingly. By aligning your organization’s network security policy with your organization’s computing strategies, you will go a long way toward mitigating risk, and keeping your data secure.
If 2017 taught us anything, it’s that everyone has to be cognizant of the treats of conducting business in the connected world. By being protective and really focusing on protecting yourself and your organization from software vulnerabilities, hackers, social engineering, and the many other threats we all face, you will be able to conduct business as usual; which, is all you can ask for with the exorbitant amount of situation that threaten the sustainability of your business.
For more information about these statistics or strategies to keep your organization from become just another victim, call Argentum IT’s IT professionals today at (502) 473-6407.


Comments